Security Brutalism Presentation: Doctrine Not Tools
A couple of weeks ago, I gave a presentation to a select group of CISOs and CIOs, introducing the foundational concepts of Security Brutalism and outlining the early work being undertaken by Black Arrows. The main focus was on the essential security fundamentals that support stronger baselines and resilience.
One of the decks presented sparked a meaningful discussion, not due to its content alone, but because many attendees observed that implementing core security controls appears to be more difficult now than it was two decades ago. Ironically, focusing on foundational security practices seems more challenging than investing billions in flashy tools that often fail to deliver on their promises
The subject of the presentation wasn’t groundbreaking, it’s not a new reality or a novel approach. But as the discussion revealed, these are fundamental principles that many organizations seem to have lost sight of.
Here's the presentation, with some of the key text that accompanies each slide. As always, it's done in a simple "Takahashi Method".
Security Brutalism: Doctrine Not Tools

OK, we are going to jump right into it: The doctrine and principles of Security Brutalism, not with shiny new tools, but with the basics.

Here's the truth: Our employees, customers, and partners are accessing our data from everywhere. It's been like this for more than a decade. If you can’t verify who's accessing what, you have no control. We must prioritize strong, centralized identity and access management above all else. This is a non-negotiable first step.

We need to move away from the mindset of “if it happens” and start thinking in terms of “it’s happening right now.” No matter how many controls are in place, an adversary will eventually find a way in. There's always an unpatched vulnerability, an exposed endpoint, or someone who clicks the wrong link.
That’s why we have to treat data, both at rest and in transit, as if our lives depend on it. We have to assume compromise is inevitable and make sure that, even if someone does get through, the data they access is useless to them.
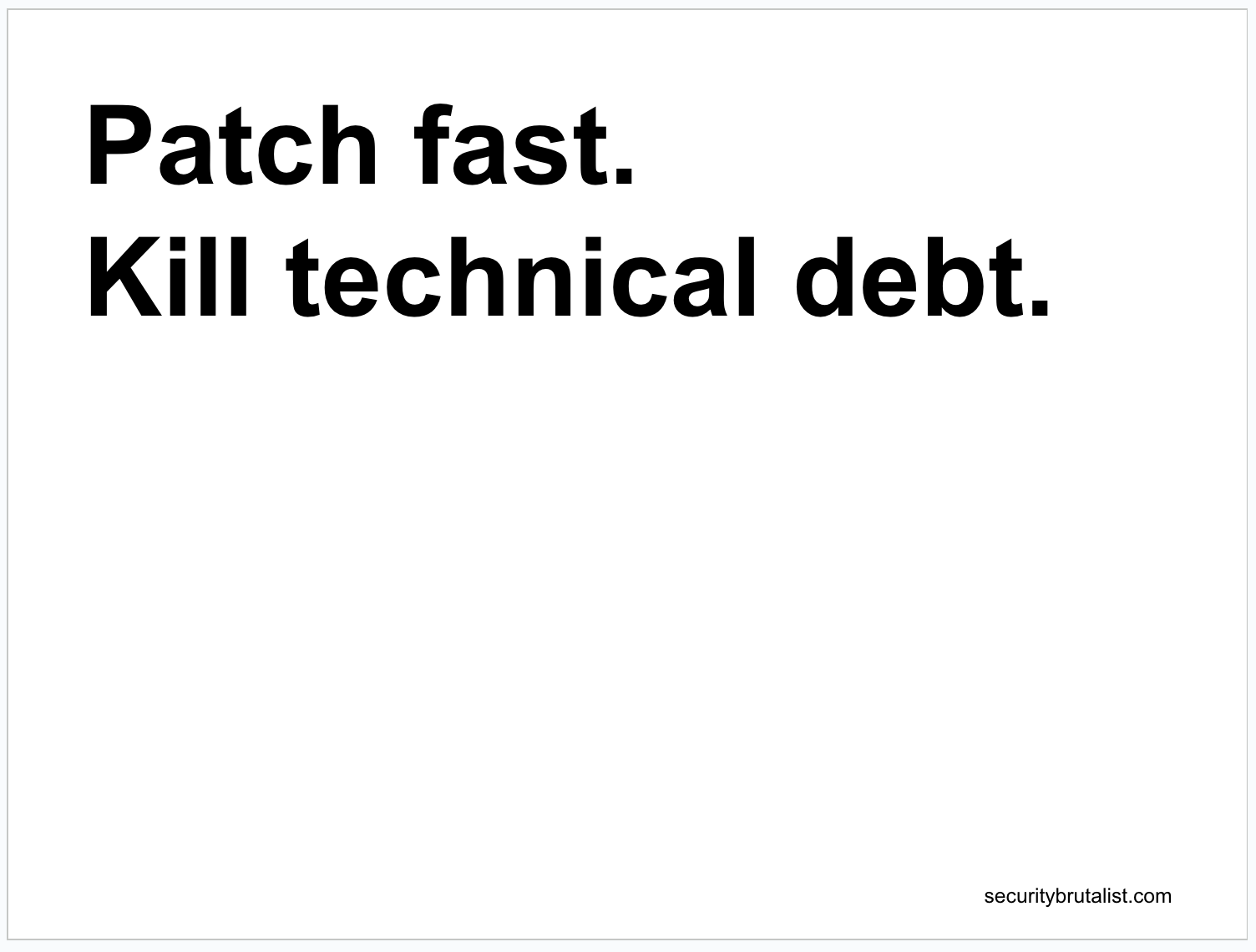
The Reality is simple: Vulnerabilities are the most common way attackers gain entry. Every unpatched system is an open invitation. Every "unpatched" human is the weakest link.
This should be our call to action. We need to streamline our patching processes and make it a top priority. Furthermore, we must actively work to eliminate technical debt. Old, legacy, unmaintained systems and code that are impossible to secure. If we can't secure it, we need to retire it. It's just an attack surface.

The principle that drives this: An attacker who gets into one part of our network should not be able to traverse freely.
We need to architect and segment our networks into small, isolated zones. But this isn't about creating complex, unwieldy network diagrams. We must also simplify our infrastructure. Again, the more complex our environment, the more attack surface we create. Simplicity is a critical defense mechanism.

Forget the buzzword. Zero trust means we never assume trust based on location or network. That's it.
In reality: Every user, every device, every application must be authenticated and authorized continuously, regardless of where they are. We verify before we grant access, and we re-verify constantly.

You can't protect what you can't see.
Collect logs from every system, device, and application. This data is our eyes and ears. Once we have the logs, we must use them to monitor our environment relentlessly for anomalous behavior. This is how we detect threats early.
Remember: Establish baselines. Look for anomalies. Have a plan.
This brings us to...

We're not talking about being pessimistic; we're talking about being realistic. Breaches are an inevitability.
We must build our security programs around the assumption that a breach will happen. This means we have a pre-planned, rehearsed incident response plan. We know exactly what to do when things go wrong because we’ve already planned for failure.
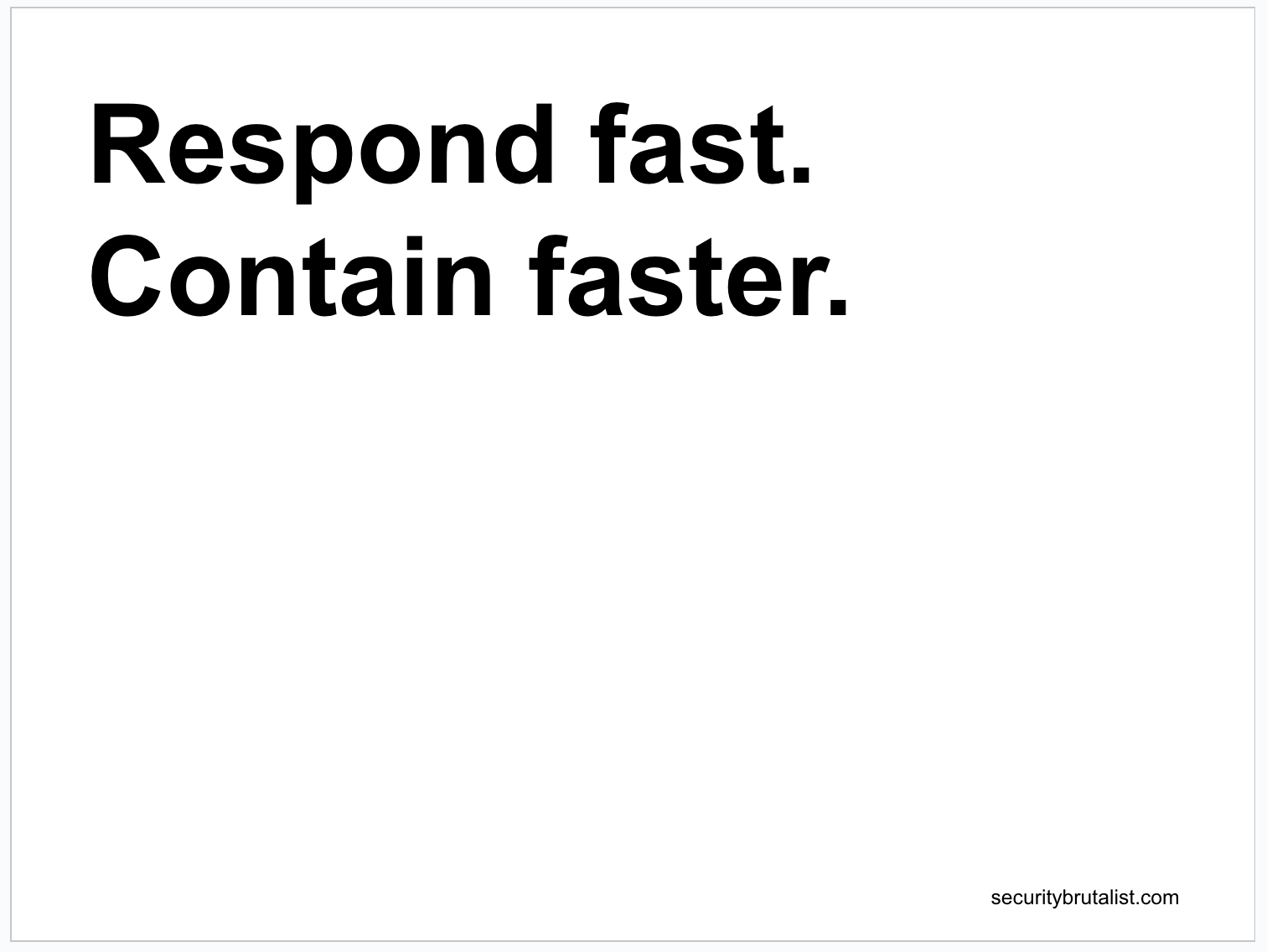
Time is our most valuable asset in a security incident. The longer an attacker is in our environment, the more damage they can do.
Compress their OODA loop under pressure, forcing rushed decisions and increasing the likelihood of mistakes. Ours should be just as fast, but driven by control and intent, not panic.
So, our response to an incident must be rapid and decisive. But our primary focus isn’t just on removing the attacker, it’s on containing the threat as quickly as possible to limit the blast radius.

Brutalist Security isn’t a checklist. It's a way of operating. It's a way of thinking. It’s an uncompromising philosophy that needs to touch our entire organization.
Security is no longer just a technical problem or a cost center. It is a core business function, and our ability to operate, innovate, and maintain trust with our customers/users depends entirely on the strength of our security doctrine.
You can download the deck as a PDF. Please ensure appropriate credit is given when using any part or all of this deck.